Basic RFID News
Solution: RFID Patrolling Tag Application, Working Principles, and Implementation
1. Application Scenarios
RFID (Radio-Frequency Identification) patrolling tags are widely adopted across industries for automated monitoring and verification. Key use cases include:
Security Patrols: Track guard routes in restricted areas (e.g., factories, data centers).
Industrial Maintenance: Verify equipment inspections in power plants or manufacturing facilities.
Infrastructure Management: Monitor routine checks of bridges, railways, or public utilities.
Healthcare Compliance: Ensure sterilization protocols in hospitals or pharmaceutical labs.
Event Management: Validate staff presence at checkpoints during large-scale events.
2. Working Principles
Core Components:
RFID Tag: A passive/active microchip with a unique ID, attached to fixed checkpoints.
Reader/Scanner: Handheld or fixed device emitting radio waves to activate tags.
Antenna: Facilitates wireless communication between tags and readers.
Software Platform: Analyzes patrol data and generates reports.
Operational Flow:
Tag Activation: The reader sends RF signals (typically 125 kHz–915 MHz) to power passive tags or receive signals from active tags.
Data Transmission: The tag transmits its unique ID and timestamp to the reader.
Data Logging: Information is uploaded to a centralized system for real-time tracking and analysis.
3. Implementation Guide
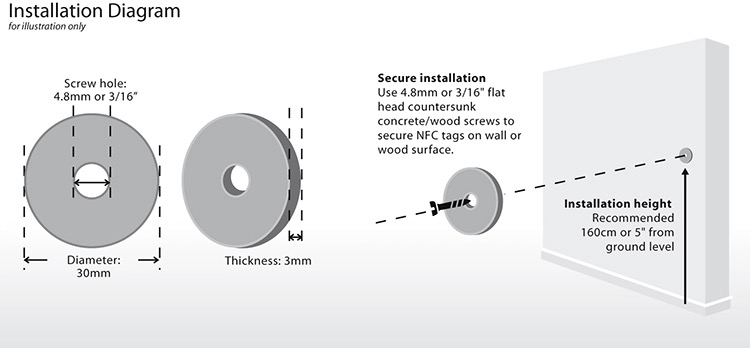
Step 1: Deploy RFID Tags
Affix tags at critical checkpoints (e.g., entrances, equipment panels).
Use ruggedized tags for harsh environments (IP67/IP68-rated).
Step 2: Configure Reader & Software
Pair handheld readers with mobile patrol apps for on-site verification.
Integrate with cloud-based platforms (e.g., AWS IoT, Azure) for data storage.
Step 3: Train Personnel
Instruct patrol staff to scan tags at designated intervals.
Define alerts for missed checkpoints or deviations.
Step 4: Execute Patrols
Personnel scan tags using readers; data syncs automatically to the backend.
Real-time dashboards display patrol progress and compliance rates.
Step 5: Analyze & Optimize
Generate audit trails for regulatory compliance.
Use AI-driven analytics to identify inefficiencies in patrol routes.
4. Case Study: Smart Factory Security
A manufacturing plant deployed RFID tags at 50 checkpoints. Guards scanned tags during rounds, achieving:
99.8% patrol accuracy.
30% reduction in manual reporting time.
Instant alerts for unauthorized zone breaches.
5. Advantages
Automation: Eliminates paper-based logs and human errors.
Scalability: Adaptable to small sites or large campuses.
Cost-Efficiency: Low hardware costs with long-term ROI.
Additional RFID Patrolling Tag Application Scenarios (2025 Update)
Here are 5 emerging and niche use cases leveraging RFID’s real-time tracking and automation capabilities:
1. Agricultural Facility Monitoring
Scenario: Track farm staff inspections of irrigation systems, livestock enclosures, or pesticide storage zones.
How It Works: Weatherproof RFID tags installed on equipment transmit scan data to IoT platforms, ensuring compliance with safety protocols.
Value: Reduces contamination risks and improves audit readiness for organic certifications.
2. Retail Asset Protection
Scenario: Monitor night-shift security rounds in warehouses or high-value retail stores.
How It Works: Tags placed near safes, inventory shelves, or emergency exits verify patrol routes. AI flags unusual gaps in scans.
Value: Combats internal theft and ensures accountability.
3. Smart Campus Safety (Schools/Universities)
Scenario: Validate security guards’ rounds in dormitories, labs, or parking lots.
How It Works: Tags integrated with emergency alert systems trigger notifications if critical zones are missed.
Value: Enhances student safety and simplifies incident investigations.
4. Renewable Energy Site Audits
Scenario: Document technician inspections of solar panels, wind turbines, or battery farms.
How It Works: Heat-resistant tags attached to equipment log maintenance history and flag overdue checks.
Value: Prevents equipment failures and supports ESG reporting.
5. Urban Waste Management
Scenario: Monitor municipal workers’ garbage collection routes and recycling bin inspections.
How It Works: Tags on bins or trucks sync scan data with city management platforms, optimizing route efficiency.
Value: Reduces operational costs and supports sustainability goals.
Why These Scenarios Matter in 2025
AI Integration: RFID data feeds machine learning models to predict risks (e.g., equipment failures, theft).
Regulatory Shifts: Stricter compliance laws in healthcare, energy, and agriculture drive adoption.
Cost Barriers Removed: Ultra-low-cost passive RFID tags (<$0.10/tag) enable mass deployment.

RELATED NEWS
CATEGORIES
LATEST NEWS
CONTACT US
Contact: June
Phone: 18018749814
E-mail: info@coretags.com
Whatsapp:+8618018749814
Add: CN,Guangdong,Shenzhen,No. 707, No. 20, Lane 4, Wayao Garden, District 33, Shanghe Community, Xin'an Street